Exercise 06: Assess Database Configurations
In this exercise, you will use Oracle Data Safe to perform a configuration assessment on your Autonomous Database (ADB). This assessment checks the database settings for compliance with security best practices, helping to identify potential vulnerabilities and areas for improvement.
Objectives
- Run a configuration assessment using Oracle Data Safe.
- Identify security risks and areas for improvement based on database settings.
Environment
Perform this exercise within the following environment:
- Compartment:
OCI-SEC-WS-LAB-nn - Region: Germany Central (Frankfurt)
- OCI Console URL: OCI Console Frankfurt - Login
- OCI User: lab-oci-sec-wsNN
- OCI Password: provided by trainer
Ensure you are in the correct compartment and region. New resources, such as Cloud Shell configurations and ADB access settings, should be created within your designated compartment.
Solution
Step 1: Explore Security Assessment
- Navigate to the Oracle Data Safe Dashboard in the OCI Console.
- Go to Data Safe -> Security Assessments.
- View the overview of the Security Assessment for your Autonomous Database (ADB).
- Select the target ADB you registered in the previous exercises.
- Explore the summary metrics such as:
- Total findings (e.g., high, medium, low risks).
- Configuration compliance score.
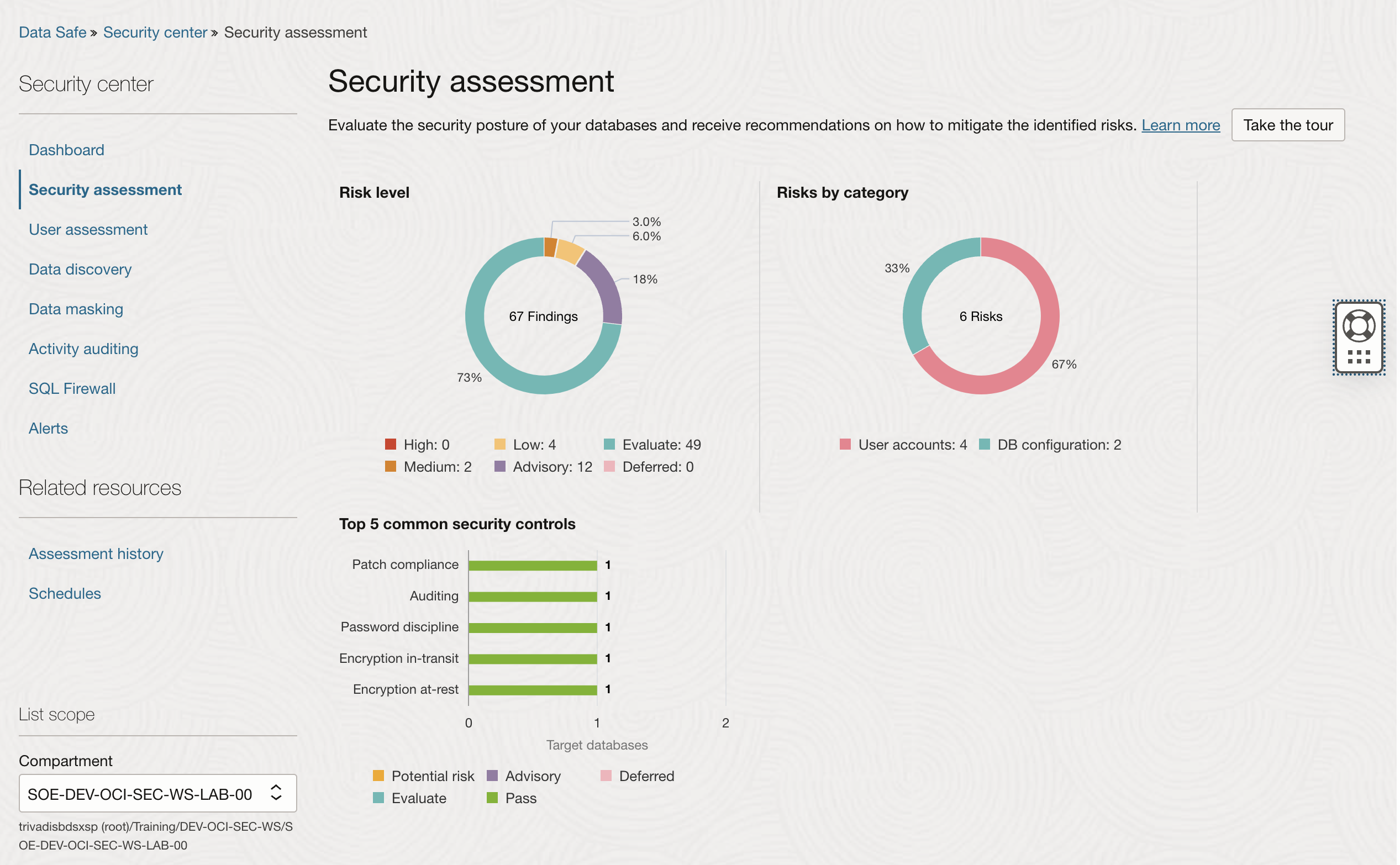
- Go to the tab Target summary and click on the latest assessment report for the ADB to review the detailed findings.
- Observe categories such as Privileges and roles, Database configuration, and Auditing.
- Note any highlighted risks or warnings in the findings.

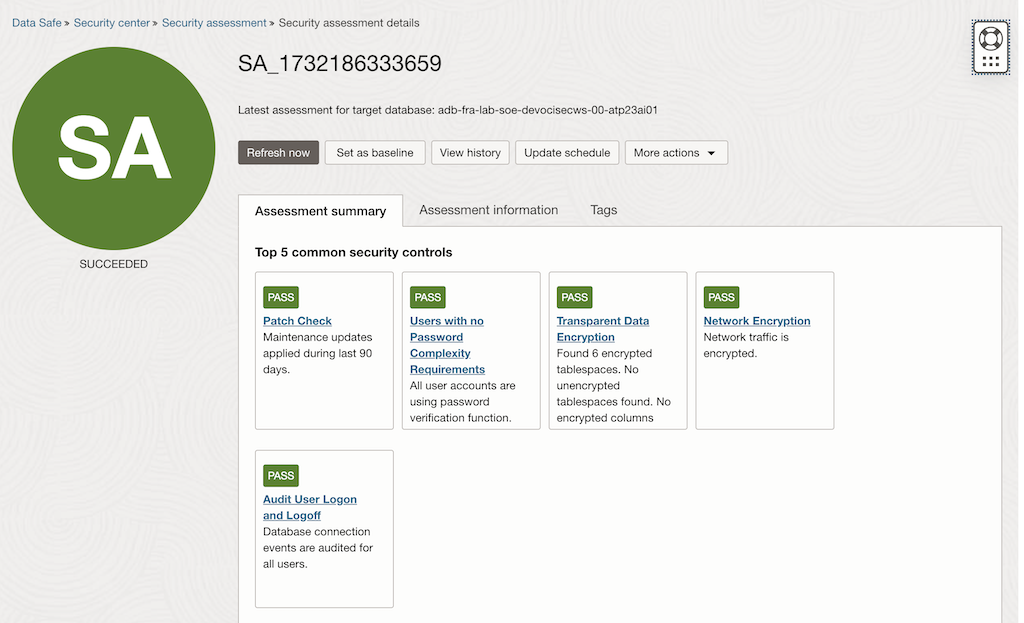
Step 2: Adjust the Risk Level of a Risk Finding
- From the Security Assessment Report, identify a risk finding that you want to adjust.
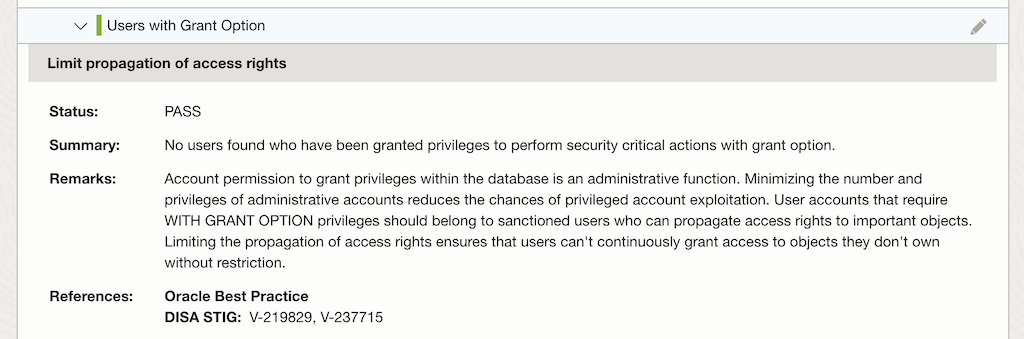
- For example: Users with Grant Option
- Click on the finding to view its details.
-
Note the current risk level (e.g., high, medium, or low).
-
- Adjust the risk level:
- Click on Edit Risk or Adjust Risk Level.
-
Select a new risk level (e.g., from “Low” to “Medium”) and provide a justification for the change (e.g., “Compliance Requirement “).
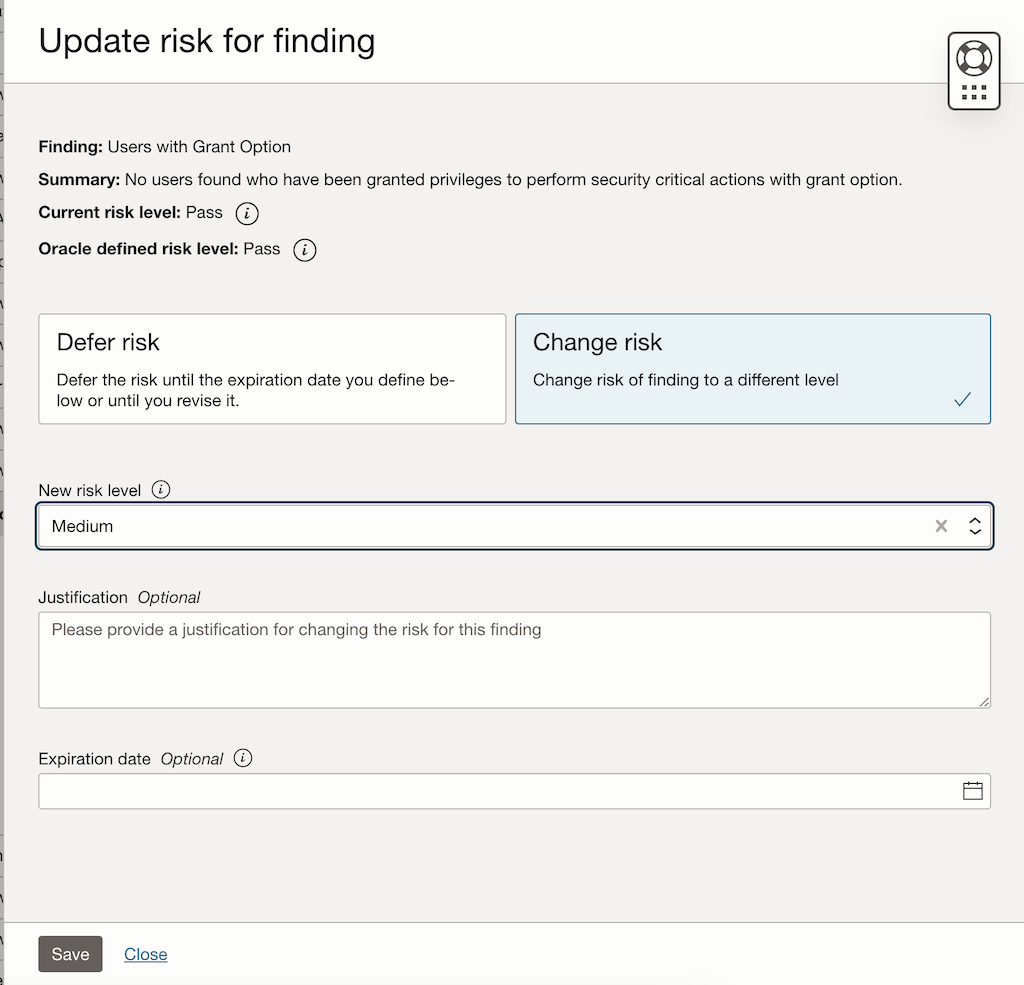
- Save the changes.
Step 3: Set Baseline
-
Go back to the top of the page of the latest assessment report for the ADB.

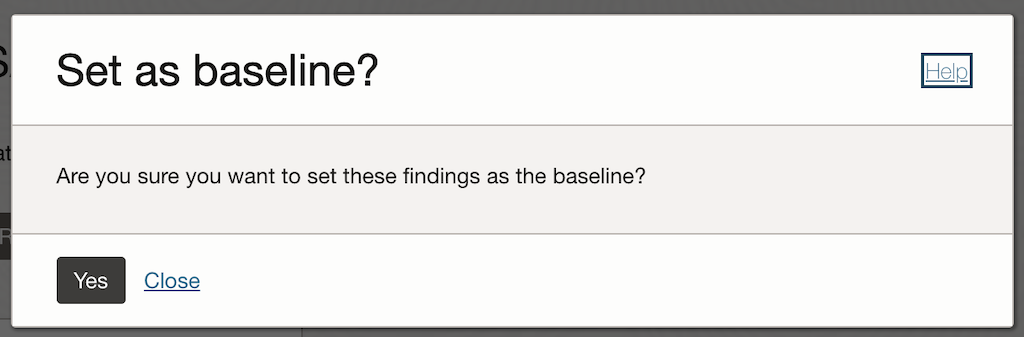
- Click on Set Baseline:
- The baseline captures the current configuration and security settings as a reference point.
- Confirm the baseline creation.
- This baseline will be used for future comparisons to identify any deviations.
Step 4: Create a Risk on the Target Database
- Simulate a security risk by modifying a configuration on the target ADB.
- Access the SQL worksheet in Database Actions. If your session has expired, sign in again as the ADMIN user.
- If needed, clear the worksheet and the Script Output tab.
-
On the worksheet, enter the following command:
GRANT alter any role TO public; CREATE USER scott IDENTIFIED BY NO AUTHENTICATION;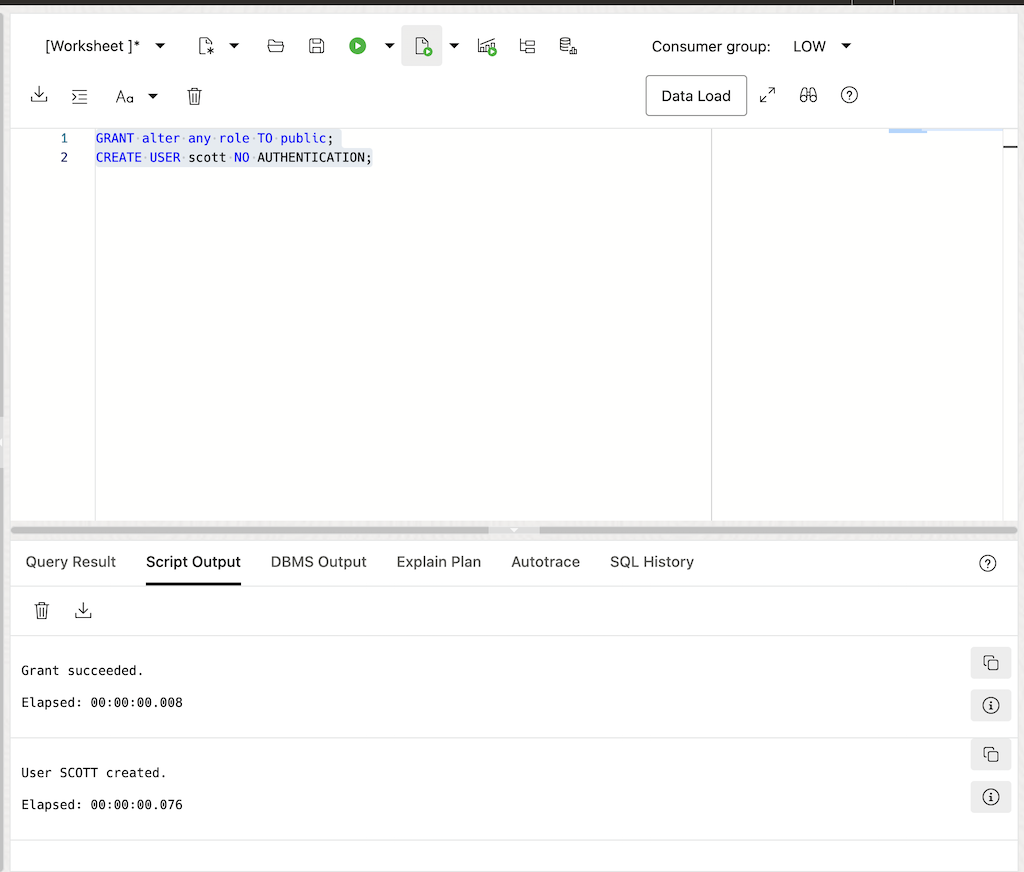
Step 5: Refresh the Latest Security Assessment and Analyze the Results
-
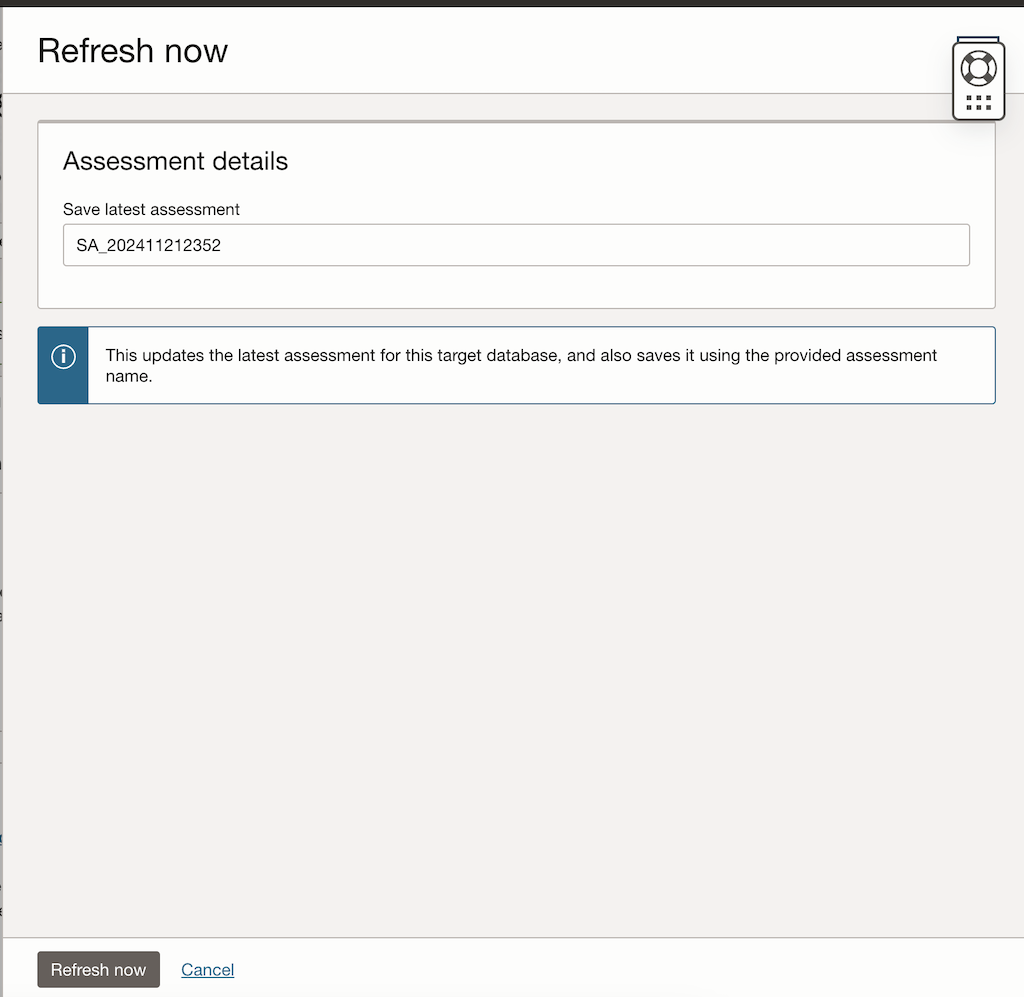
Navigate back the top of the page of the latest assessment report for the ADB.
- Click Refresh Assessment:
- Wait for the assessment to complete.
- The new assessment should reflect the risk you introduced in Step 4.
- Analyze the updated assessment report:
- Look for the new risk findings created by your changes.
- Review the affected areas and recommendations provided by Data Safe.
Step 6: Compare Your Assessment with the Baseline
-
From the Security Assessments page, select the Baseline Comparison option.
- Compare the latest assessment results with the previously set baseline.
- Identify any deviations or new risks.
- Note changes such as:
- Configuration setting differences.
- Additional risk findings introduced in Step 4.
- Document the results of the comparison:
- Highlight any areas of concern that should be addressed.
- Reset the baseline if the new state is acceptable and reflects the desired configuration.
Summary
In this exercise, you:
- Performed a configuration assessment with Oracle Data Safe to evaluate database settings.
- Identified potential vulnerabilities and areas to enhance security compliance.
You are now ready to continue with the next exercise, where you will assess database users to further strengthen your security posture.
- Previous Exercise: Exercise 05: Data Safe Configuration and Register ADB
- Next Exercise: Exercise 07: Assess Database Users